Smart contracts do not fail randomly. They fail in patterns.
Over the last several years, blockchain systems have experienced recurring classes of catastrophic loss. Postmortems are written. Root causes are debated. Code is patched.
What has been missing is structured prioritization of which failure modes matter most.
The OWASP Smart Contract Top 10 (2026), published under the OWASP Foundation, provides that structure. It is a forward-looking risk classification framework derived from real-world exploit data and practitioner input across auditors, protocol engineers, and incident responders.
Why Web3 Requires a Standardized Risk Framework
Application security matured in Web2 because of standardized taxonomies. Frameworks such as:
- OWASP Foundation Top 10 for web applications
- MITRE Corporation Common Weakness Enumeration
- National Institute of Standards and Technology cybersecurity risk frameworks
These enabled organizations to align engineering, security, governance, compliance, and board-level reporting.
Web3 has historically relied on point-in-time audits, reactive patching and bug bounties.
The OWASP Smart Contract Top 10 shifts the discipline toward a baseline doctrine:
If a risk class has repeatedly caused financial loss in production, it must be treated as a design constraint.
How Smart Contracts Actually Fail in Production
Across major incidents, the lifecycle typically follows:
- A design assumption is made
- Code reflects that assumption
- Privilege or dependency exposure exists
- An adversary identifies economic amplification path
- Valid transactions are executed at scale
- Capital exits the system
Notice what is absent:
• Broken cryptography
• Random bytecode errors
• Exotic zero-days
The failures are structural. The Top 10 identifies where those structures collapse.
The OWASP Smart Contract Top 10 (2026) Structural Overview
Below is a production focused interpretation of each category.
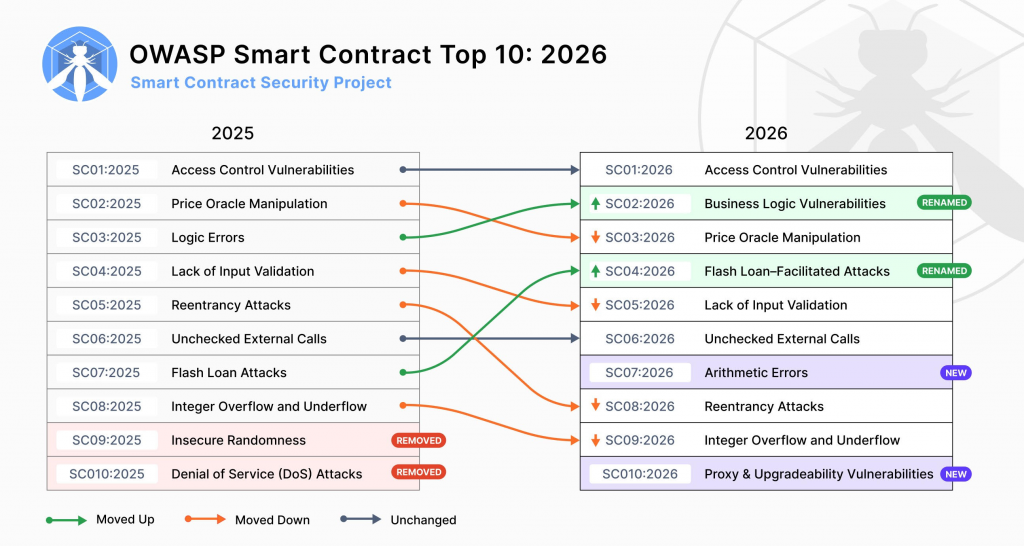
| ID | Risk Category | What It Means in Production | Common Exploit Patterns | Why It Repeats | Core Mitigations |
|---|---|---|---|---|---|
| SC01:2026 | Access Control Vulnerabilities | Improper restriction of privileged functions or roles | •Overpowered admin keys • Missing onlyOwner checks • Role escalation • Governance takeover • Treasury drain via compromised key | Authority not bounded by blast radius; privilege concentration | • Role segmentation • Timelocks • Multi-layer authorization • Privilege audits • Withdrawal limits |
| SC02:2026 | Business Logic Vulnerabilities | Flaws in protocol rules, state transitions, or economic assumptions | • Incorrect reward distribution • Broken staking math • Improper liquidation logic • Exploitable incentive loops | Protocol assumptions break under adversarial conditions | • Explicit invariant modeling • Adversarial simulations • Scenario testing • Formal verification where feasible |
| SC03:2026 | Price Oracle Manipulation | Exploitation of external pricing inputs to manipulate protocol state | • Liquidity pool manipulation • Low-liquidity oracle distortion • Stale feed usage • Sandwich amplification | Over-reliance on manipulable onchain prices | • Time-weighted averages (TWAP) • Multi-source oracles • Liquidity thresholds • Circuit breakers |
| SC04:2026 | Flash Loan Facilitated Attacks | Use of uncollateralized loans to manipulate protocol logic within a single transaction | • Governance vote manipulation • Oracle distortion • Temporary liquidity inflation • Capital-free arbitrage abuse | Protocol logic assumes capital persistence | • Flash-loan-resistant design • Snapshot voting • Time-weighted voting power • Slippage & liquidity guards |
| SC05:2026 | Lack of Input Validation | Failure to sanitize or constrain function parameters | • Arbitrary address injection • Invalid state transitions • Excessive loop parameters • Zero-value edge cases | Contracts trust user input without boundaries | • Parameter bounds checks • Input sanitization • State validation modifiers • Defensive programming |
| SC06:2026 | Unchecked External Calls | Ignoring return values or failing to handle external call failures | • Silent call failure • Fallback misuse • Token transfer without verification • Callback exploitation | Composability assumed safe by default | • Check return values • Use try/catch patterns • Minimize trust in external contracts • Reentrancy guards |
| SC07:2026 | Arithmetic Errors | Incorrect calculations affecting balances, rewards, or supply | • Precision loss • Rounding exploitation • Division errors • Reward inflation | Improper fixed-point math handling | • Safe math libraries • Precision-aware calculations • Unit tests for edge cases |
| SC08:2026 | Reentrancy Attacks | Recursive contract calls exploit state changes before updates finalize | • Withdraw-before-update exploit • Cross-contract reentrancy • Callback exploitation | Improper order of state updates and external calls | • Checks-Effects-Interactions pattern • Reentrancy guards • Pull over push payments |
| SC09:2026 | Integer Overflow and Underflow | Numeric wraparound errors altering balances or limits | • Balance overflow • Negative value wraparound • Supply miscalculation | Improper handling of numeric boundaries | • Solidity 0.8+ built-in checks • Safe math validation • Boundary testing |
| SC10:2026 | Proxy & Upgradeability Vulnerabilities | Misconfiguration of upgradeable proxy patterns | • Storage collision • Admin hijack •Implementation swap • Upgrade without delay | Upgrade authority not constrained or audited | • Upgrade timelocks • Transparent proxy patterns • Storage layout validation • Governance hardening |
Mapping the Top 10 to the Smart Contract SDLC
Security alignment must occur across lifecycle phases.
Design Phase
• Threat modeling mapped to Top 10 categories
• Privilege boundary documentation
• Economic adversary modeling
Development Phase
• Static analysis
• Role fuzzing
• Invariant testing
• External call surface review
Audit Phase
• Explicit mapping of findings to Top 10 categories
• Severity prioritization by systemic impact
Deployment Phase
• Timelock enforcement
• Parameter bounds verification
• Monitoring activation
Post-Deployment Phase
• Privilege drift detection
• Invariant monitoring
• Governance activity alerts
Framework alignment must persist beyond audit completion.
Enterprise Governance Integration
For institutional participants, the Top 10 supports:
• Risk register alignment
• Vendor due diligence
• Board reporting
• Change control processes
• Regulatory defensibility
It creates shared language between:
• Engineering
• Security
• Compliance
• Executive leadership
Framework alignment reduces systemic ambiguity.
Startup Survival Implications
Early-stage teams often:
• Centralize authority for speed
• Defer governance hardening
• Underestimate oracle exposure
• Overlook blast radius constraints
The Top 10 provides a pre-mainnet checklist.
Security maturity signals improve:
• Investor confidence
• Exchange readiness
• Institutional partnerships
Security doctrine is strategic positioning.
Security Maturity Levels
Level 1: Audit-dependent
Level 2: Checklist-aware
Level 3: Framework-aligned
Level 4: Runtime-monitored
Level 5: Adaptive governance
Progression requires operationalizing Top 10 categories into:
• Engineering workflows
• Governance policy
• Monitoring infrastructure
2026 Risk Signals
The 2026 prioritization reflects growing concerns around:
• Privilege drift in mature protocols
• Governance accumulation attacks
• Cross-chain settlement exposure
• Infrastructure-assisted compromise
• AI-assisted exploit reconnaissance
Security posture must evolve from reactive patching to structural resilience.
Self-Assessment Questions
• Are all privileged actions formally documented?
• Is upgrade execution delayed and monitored?
• Are economic invariants encoded and tested?
• Are external dependencies redundantly validated?
• Is governance resistant to rapid accumulation attacks?
• Are privilege changes continuously monitored?
If multiple answers are unclear, structural risk exposure exists.
Check if you are security ready in 2026, take the challenge: https://credshields.com/resources#2026-security-readiness-checklist
End Word
Smart contract exploits are rarely unprecedented. They are recurring structural failures.
The OWASP Smart Contract Top 10 (2026) provides a production-driven prioritization model grounded in real incident patterns.
Security in Web3 must mature from audit-centric thinking to structured failure prevention. The Top 10 is the baseline.
